My Store
Self Paced Course - Hacking Hardware Debuggers
Self Paced Course - Hacking Hardware Debuggers
Couldn't load pickup availability
Hacking Hardware Debuggers - A Self Paced Course
Do you want to learn how to reverse engineer and attack hardware level debug interfaces like JTAG and SWD? Do these interfaces feel like a black box to you and you would like to learn more about how they work internally?
This online course features the JTAG and SWD portions of our extremely popular Hardware Hacking Bootcamp!
Do you want a preview of the content/teaching style? Check out the following resources:
- Hacking Hardware Debuggers - Remoticon Talk
- Hackers Guide to JTAG
- Hackers Guide to SWD
- JTAG Hacking with a Raspberry Pi
Description
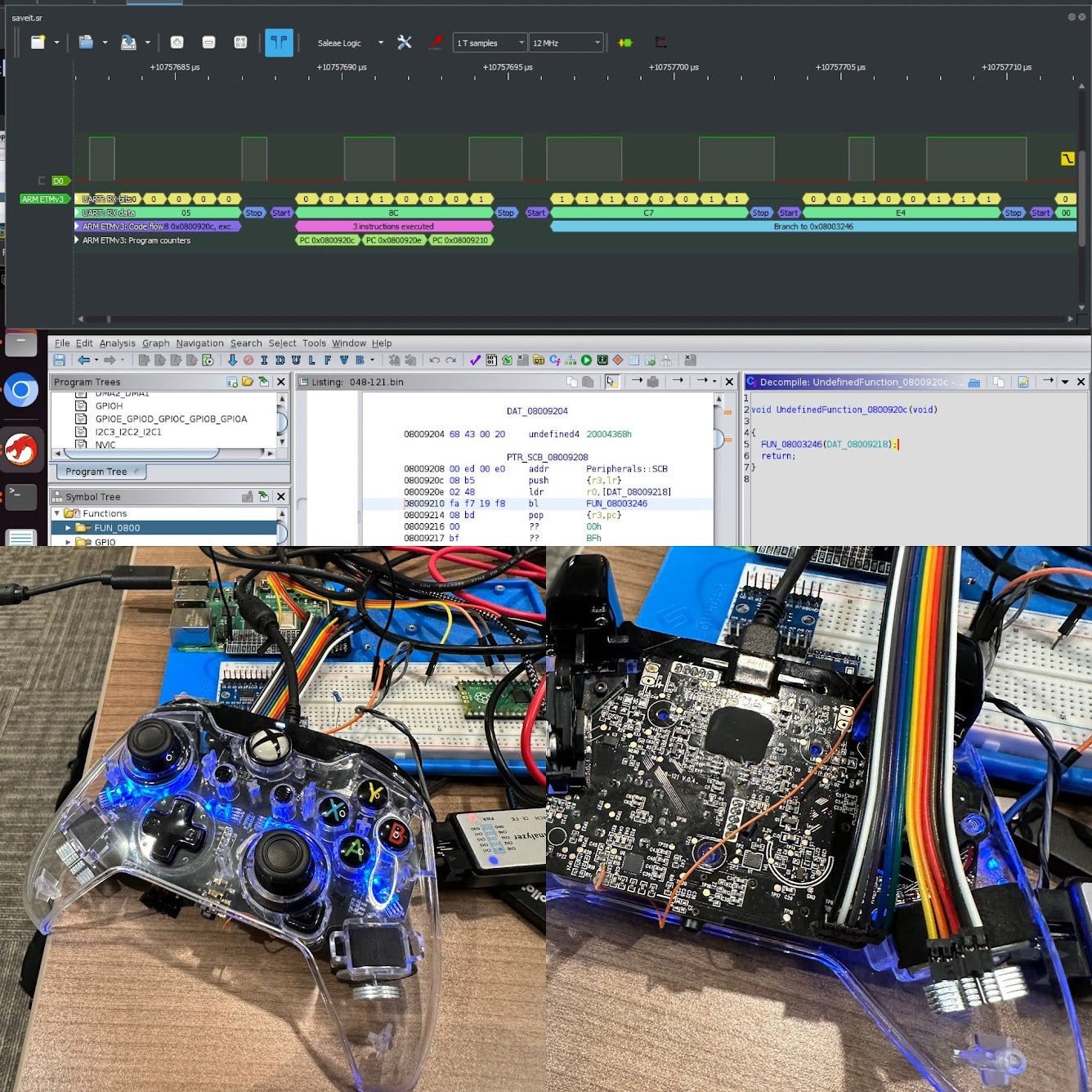
This course teaches students how to identify, instrument, and utilize hardware-level debuggers. Focusing on JTAG - Joint Test Action Group and SWD - Serial Wire Debug, students will first learn to use these interfaces on an exemplar target and then test their abilities on a commercial-off-the-shelf (COTS) target.
Have you ever tried to use OpenOCD or other open source hardware level debuggers, only to become overwhelmed with config files, patches and obtuse error messages?
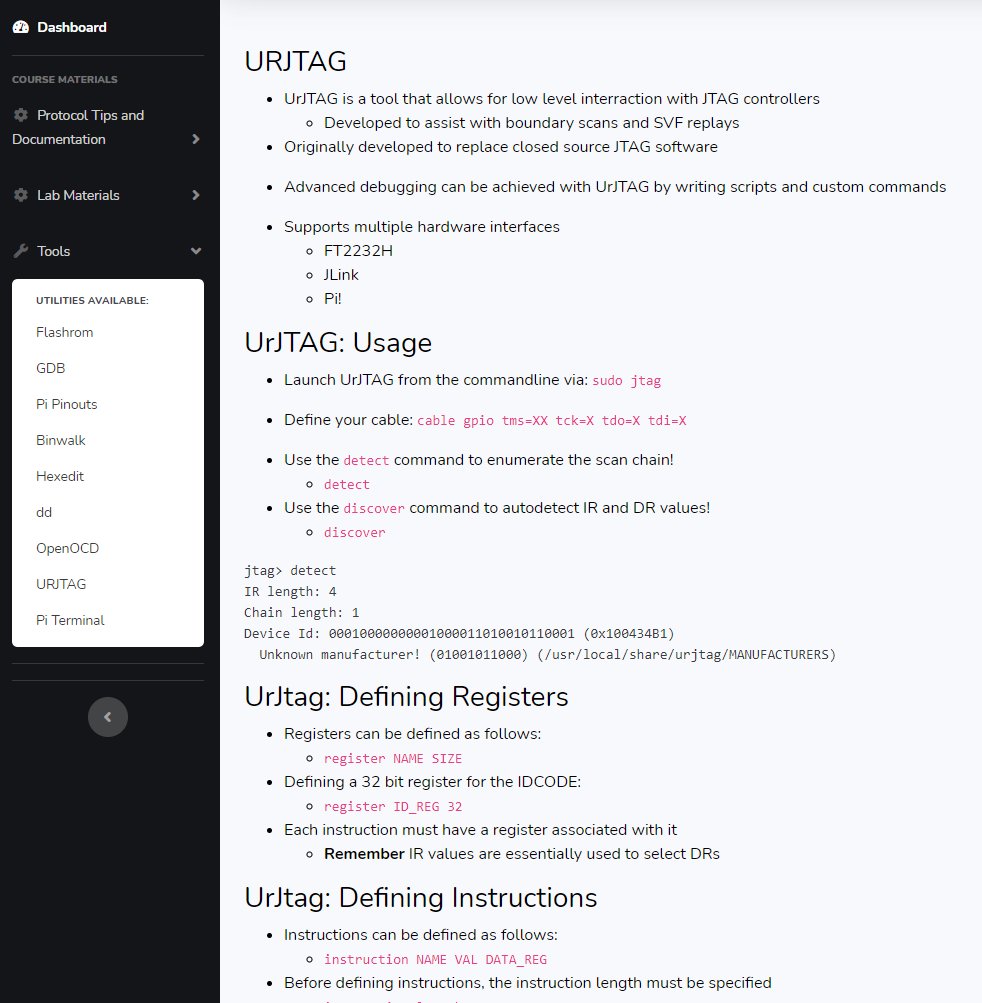
Students will learn how to interact with these interfaces at the signal level and develop high-level tools through labs and exercises. After writing tools to instrument the target, students will utilize tools such as UrJTAG and OpenOCD to gain access to the target systems.
Course Objectives
After participating in this course, students will:
- Identify and interface with a JTAG test access port
- Manually instrument and navigate JTAG scan chains
- Develop OpenOCD config files for high-level JTAG access
- Utilize JTAG to extract RAM from a target device and modify its behavior
- Understand how the SWD protocol is implemented
- Use SWD to read and write memory manually
- Extract and modify flash memory via SWD using OpenOCD
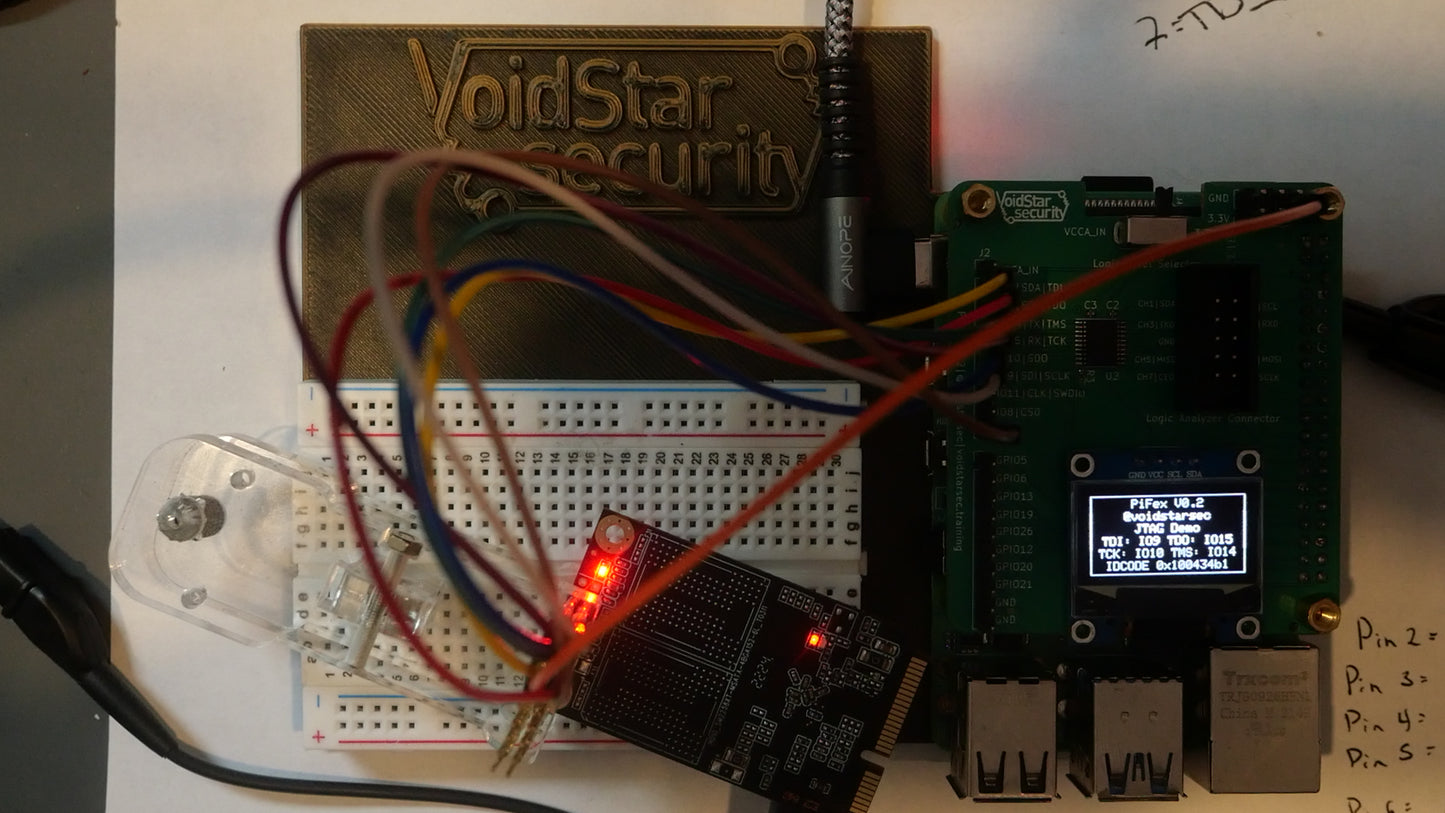
Students will utilize open source tooling and develop tools to interface with the targets included in the kit. All exercises and laboratories are performed using open source tooling on a Linux-based SBC. The targets in the kit include a development board (for learning purposes) and then a COTS target for each interface being targeted.
Upon completion of the course, students will receive:
- A certificate of completion
- All slides for the course materials
- Video recorded lectures from the course (if remote)
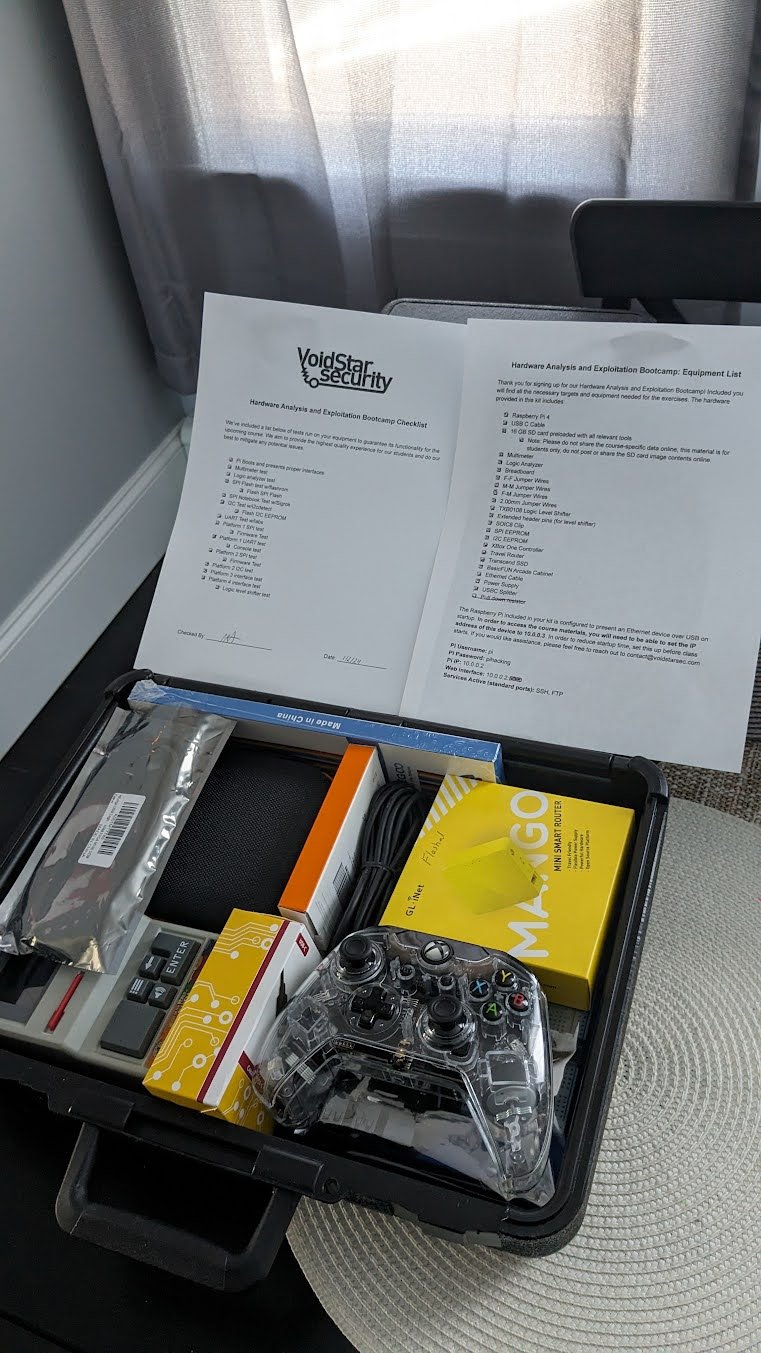
- An SD card containing the software and tooling used for the Linux based SBC
- Access to a Discord channel with past students of VSS courses
Course Structure
This course is primarily made up of practical exercises. Students will first instrument the target devices manually using python-based tooling and pre-existing tools. An outline and task list for each module can be found below.
1. Hardware Debugging Overview and History
a. Purpose of Hardware Debugging
b. Past and Present Debug Standards
c. ARM ADI Specification Review
d. Hardware Kit Setup and Review
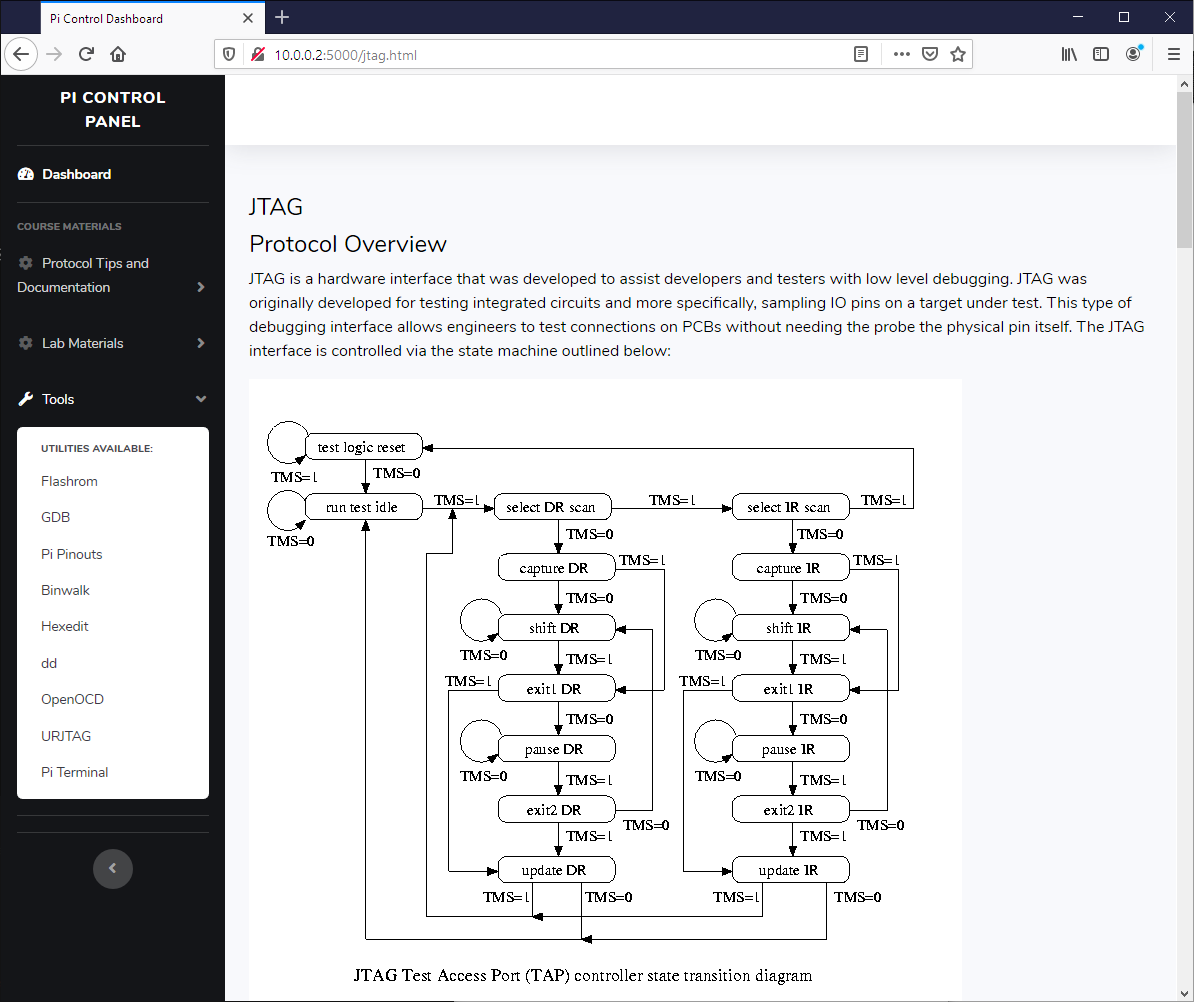
2. JTAG Protocol Review
a. History of JTAG Specification
b. Practical Applications of JTAG
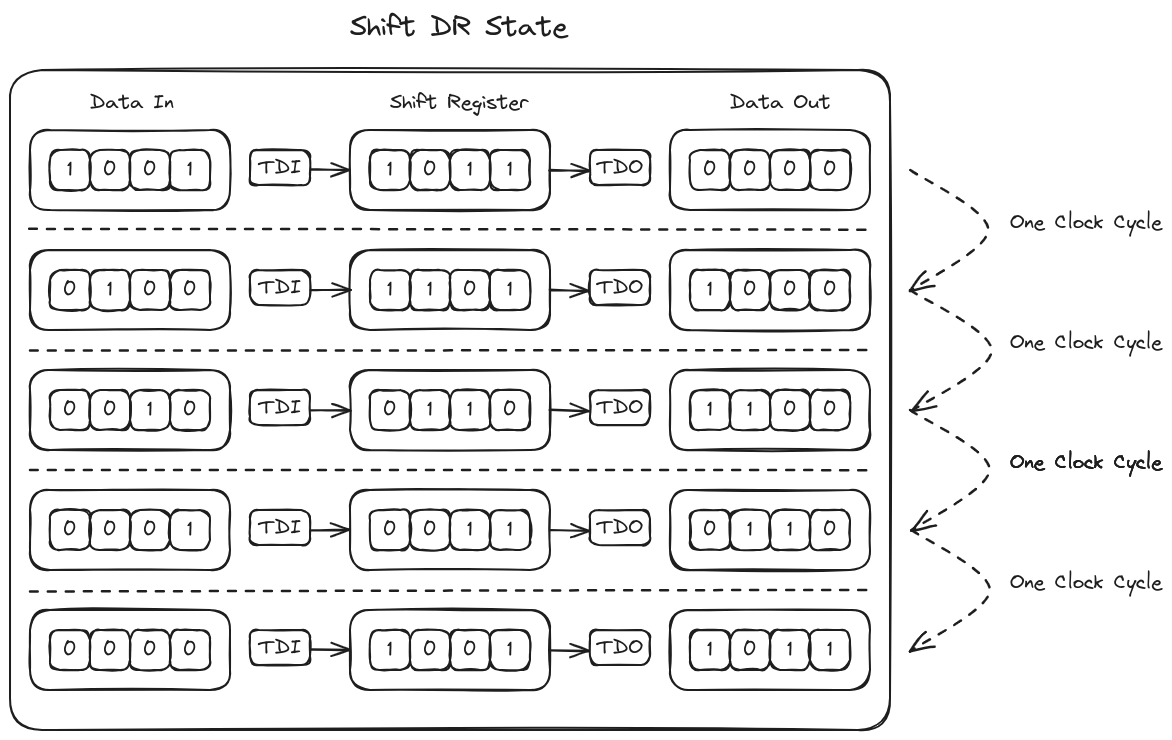
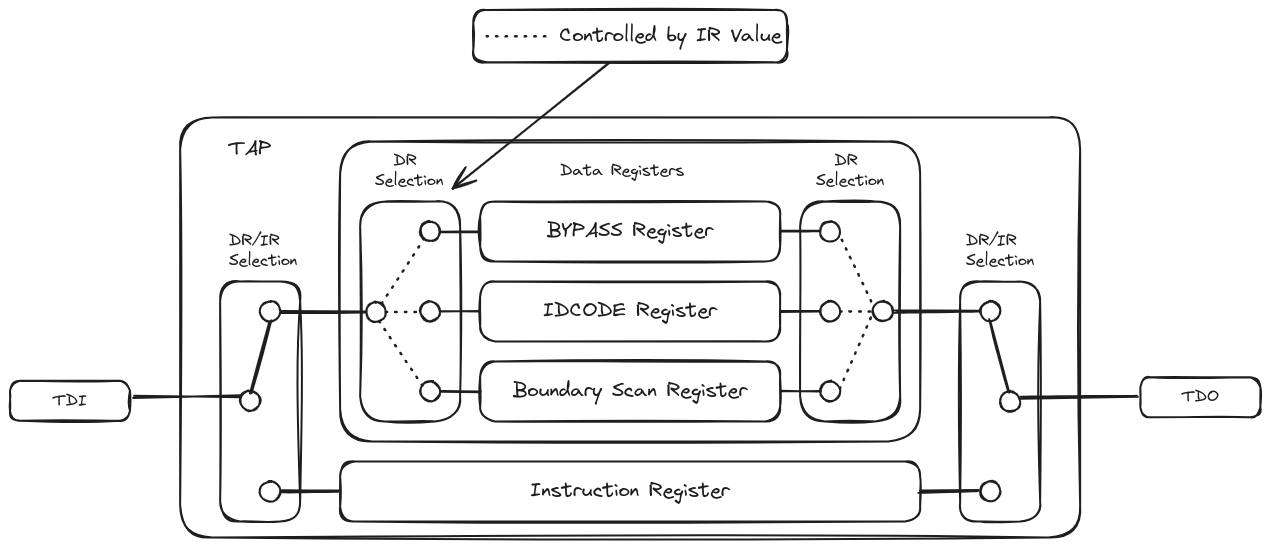
c. State Machine Navigation
c. Register Usage and Access
c. JTAG and ARM ADI Integration
3. JTAG for Reverse Engineers:
a. How to Identify JTAG Test Points
b. Detecting Pinouts via ID CODE
c. Detecting Pinouts via BYPASS
d. How to Determine Register Length
e. Manually Navigating the State Machine
3. JTAG Exercises: Examplar Development Board
a. Identify JTAG Pinout
b. Determine Register Length
c. Manually Extract ID CODE
d. Manually Read/Write Memory
e. Develop OpenOCD Configuration
4. JTAG Exercises: Target - Transcend SSD
a. 3.a - 3.e
c. Debug SSD Using GDB
b. Modify SSD Read Operation
d. Modify Firmware on SSD via JTAG
5. SWD Protocol Review
a. History of SWD Specification
b. Practical Applications of SWD
c. SWD Packet Structure and Format
c. SWD and ARM ADI
d. SWD ADI Examples
6. SWD Exercises: Exemplar Development Board
a. Identify SWD Pinout and Extract ID
b. Manually Read/Write Memory Regions
c. Read/Write Memory via OpenOCD
d. Extract Flash via OpenOCD
e. Modify Firmware and Reflash via OpenOCD
Target Audience / Prerequisites
This course is targeted toward IT professionals and security researchers who want to learn more about how hardware-level debuggers work and how to approach them as a reverse engineer. Students should be familiar with the Linux command line and be comfortable with a scripting language such as python. C experience is also helpful but not required. While some hardware experience will be beneficial, it is not required for this course.
Purchase of this course includes:
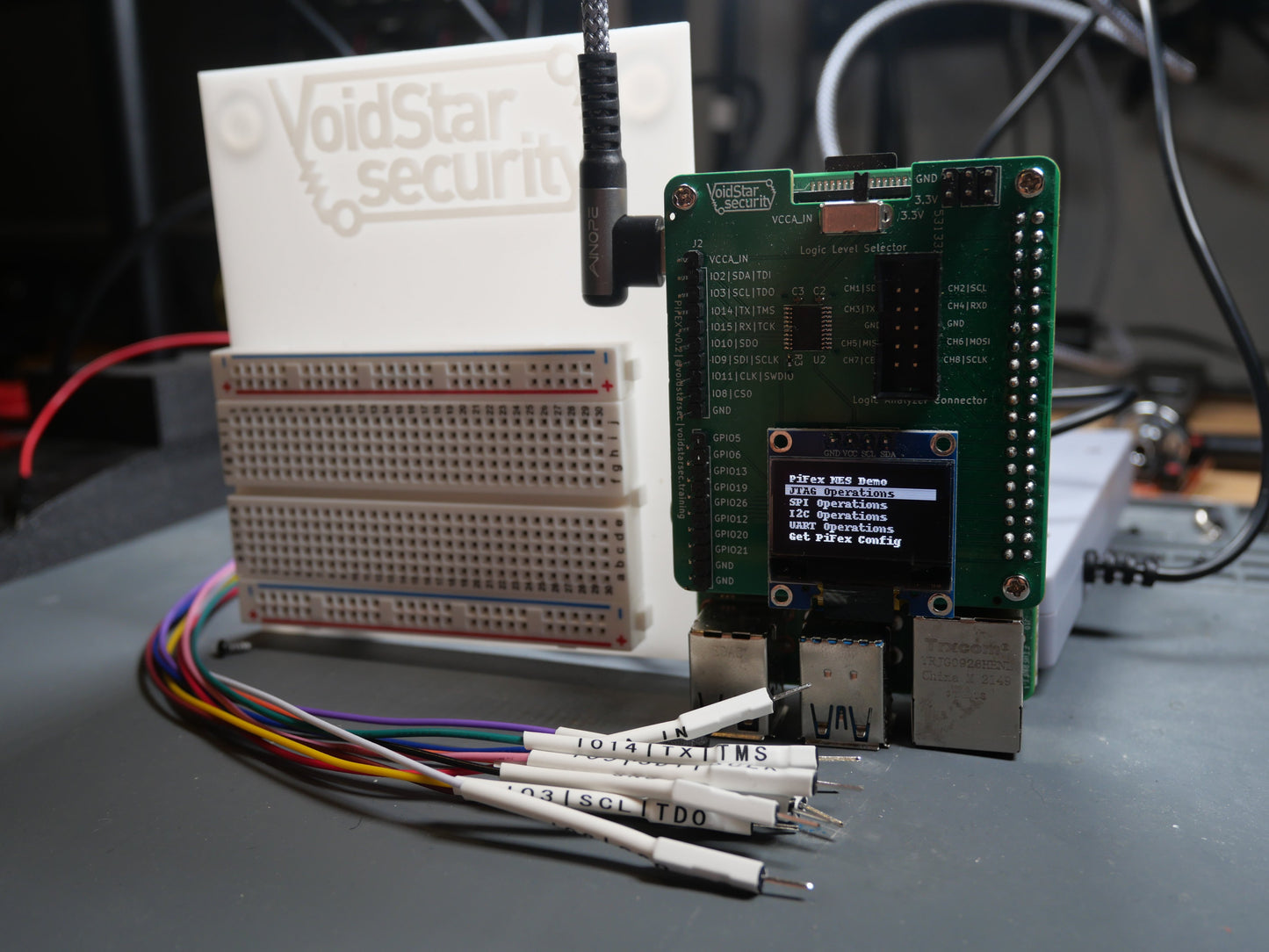
- Hardware kit containing all required materials
- PiFex Kit
- JTAG Target(s)
- SWD Targets
- Logic Analyzer
- Multimeters
- Jumper wires, breadboard, carrying case
- PiFex Kit
- 3 month access to the online course materials
- Access to weekly office hours for live Q&A
Share